Industry Thought Leadership
Implications of 5G on Cybersecurity
February, 2020Telecommunications networks have laid the foundation for the technologies that the world depends on. Owing to their scale and criticality, mobile operators have become a major target for cyber-attacks. The data boom that accompanied 4G created vast amounts of valuable data for the telecommunications industry and the same can be expected at a much larger scale with the proliferation of new technologies like 5G and IoT. Specifically, 5G’s network design brings about a number of upgrades to the network infrastructure that consequently implies network security challenges that require careful and effective mitigation.
1. Cybersecurity concerns posed by 5G
5G entails several infrastructural modifications to traditional telecoms networks that could pose increased security risks. The most critical security risks / concerns posed by 5G are as follows –
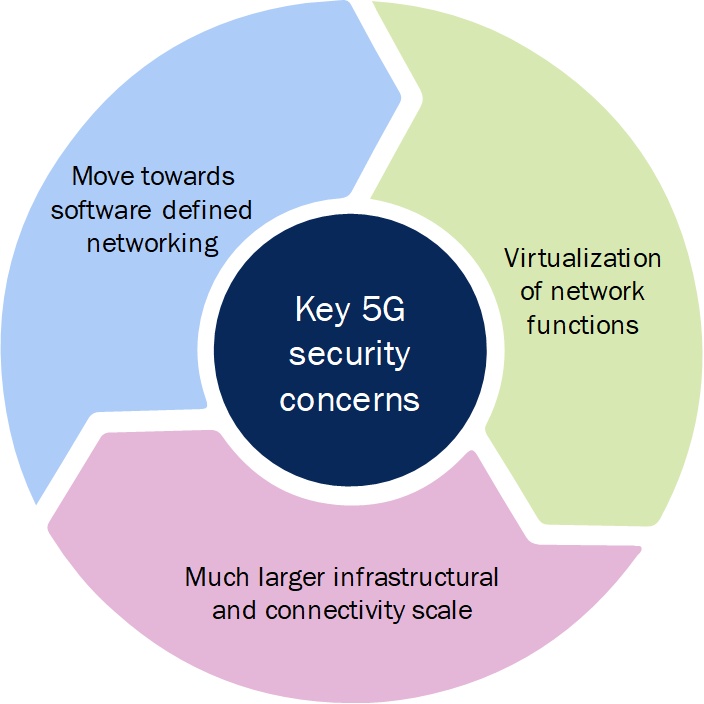
Figure 1: Key cybersecurity concerns posed by 5G [Source: Analysys Mason]
- Move towards software defined networking: which leads to a decentralization of core functions that were originally centralised and hence, well protected
- Virtualization of network functions: which can increase the risk of cyber-attacks because providing the same level of security as physical appliances will be difficult
- Much larger scale: with the expected large-scale proliferation of small cells and the number of connections (IoT-enabled devices running on 5G), the number of attack vectors for cyber-attacks will increase significantly
Among the security risks highlighted above, a key risk that needs to be elaborated on is that the distinction between core and edge networks is expected to diminish with the advent of 5G. Due to its network design, sensitive functions that are currently performed in the separated core are expected to gradually move closer to the edge of the network. This is believed to provide ways to circumvent traditional security controls affecting the overall network integrity, availability as well as the confidentiality of customer data.
2. Steps taken by global 5G leaders to address such concerns
In order to address these network security concerns, careful and effective risk mitigation is required. Governments and telecom regulators typically establish regulations on cybersecurity, however, only a handful of countries have taken notice of the increased security requirements of 5G and addressed the security gap. Australia, the United States and Germany are among the countries leading the charge to develop stricter cybersecurity regulations for 5G.
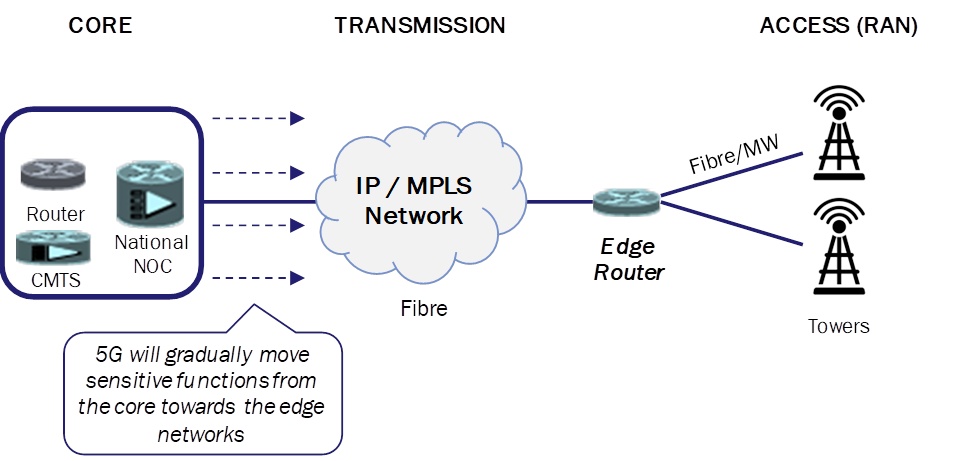
Figure 2: Shift of sensitive functions from the core towards the edge due to 5G [Source: Analysys Mason]
2.1 Australia
Owing to the increased security requirements of 5G, in August 2018, the Australian Government’s Department of Home Affairs released regulations regarding cybersecurity titled ‘Telecommunications Sector Security Reforms’ (TSSR). The key elements of the regulation include:
- Service providers are to protect their networks and facilities from unauthorised access or interference to ensure their availability, integrity and confidentiality of communications
- Involvement of vendors deemed likely to be subject to extrajudicial directions from a non-Australian government seen as a risk to the protection of 5G networks
- Service providers to maintain competent supervision and effective control over networks including arrangements to maintain visibility of operations, data flow and locations
- Providers to notify the government of proposed changes to their networks and services that can compromise their ability to comply with the security obligations
- Minister for Home Affairs to have the power to direct a service provider or intermediary to do (or not do) a specified thing that is reasonably necessary to protect networks and facilities from national security risks
2.2 Germany
In October 2019, the German telecommunications regulator Bundesnetzagentur published a new draft catalogue with security requirements. It require providers of telecommunications services to prepare and implement appropriate security measures, with the objectives of protecting communications secrecy, preventing data breaches, preventing network and service interruptions and manage security risks.
While 5G and international security concerns might be the catalyst for these requirements, they will be applied across all networks and communications infrastructure moving forward, as well as all vendors. The following security requirements are planned for the telecommunications networks:
- Systems to only be sourced from trustworthy suppliers who comply with national security regulations and provisions for the secrecy of telecommunications and data
- Network traffic to be monitored regularly for any abnormality and appropriate protection measures to be taken in case of a concern
- Only certified security-related network and system components to be used
- Only trained professionals to be employed in security-related areas and professionally competent, reliable and trustworthy contractors to be selected for system-related process outsourcing
Adequate redundancy to be available for critical, security-related network and system components
2.3 United States of America
In July 2019, the US’ Cybersecurity & Infrastructure Security Agency (CISA) released a Critical Infrastructure Security and Resilience Note pinpointing the security concerns that the agency identifies for 5G. The agency highlighted that the use of 5G components manufactured by untrusted companies could expose US entities to risks especially since the technology will use more components than previous generations of wireless networks.
The report suggested several measures the US Government could take to reduce the risks of deploying a 5G network including:
- Use of 5G network components manufactured by trusted companies since the proliferation of the technology’s infrastructure may provide malicious actors more attack vectors
- Promoting open, transparent and consensus–driven international standards and processes that do not place trusted companies at a disadvantage
- Limiting the adoption of 5G equipment with known or suspected vulnerabilities
- Development of trusted 5G technologies, services, and products
2.4 Summary of the measures taken
There are several overlapping objectives and procedures that have been observed in the steps taken by the three countries. Each have clearly highlighted the underlying concerns and objectives of the new requirement including consumer protection, business protection and/or national security. Moreover, the areas of focus within these requirements include codes of conduct, monitoring obligations, choice of vendor/supplier, standards of equipment, staff and stakeholder measures and notification requirements.
The figure below highlights the commonalities in the approach taken by Australia, USA and Germany to address 5G cybersecurity concerns.
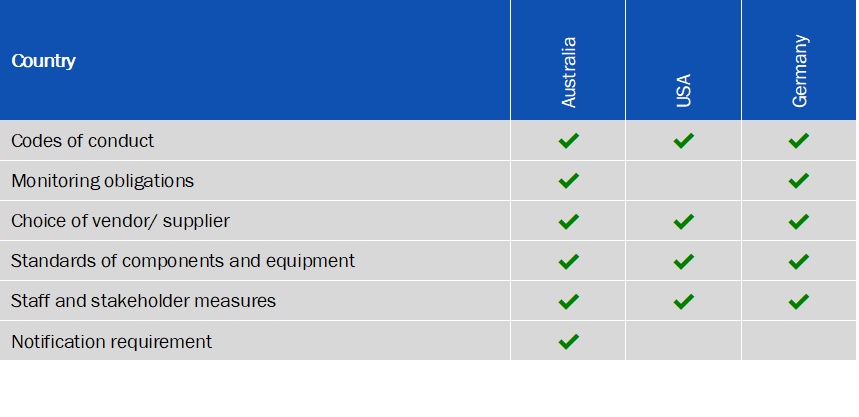
Figure 3: Measures taken by the three countries for 5G cybersecurity

